This $15 board beats Android phone fingerprint sensors

According to researchers, bypassing the fingerprint sensor of Android devices is only possible with a $15 board. The fingerprint sensor is one of the most common features of Android phones. This feature increases security because it only allows entry with the smartphone or tablet holder’s fingerprint. Of course, this solution is not as secure as imagined because, as researchers say, bypassing the fingerprint authentication system of Android devices is only possible with a $15 board.
The hack board for Android fingerprint sensor is called BrutePrint and it takes about 45 minutes to bypass the sensor. Researchers tested this method on 10 smartphones, including the iPhone SE and iPhone 7, to demonstrate the features of BrutePrint. Some high-end phones and some older Android devices were also included in this test.
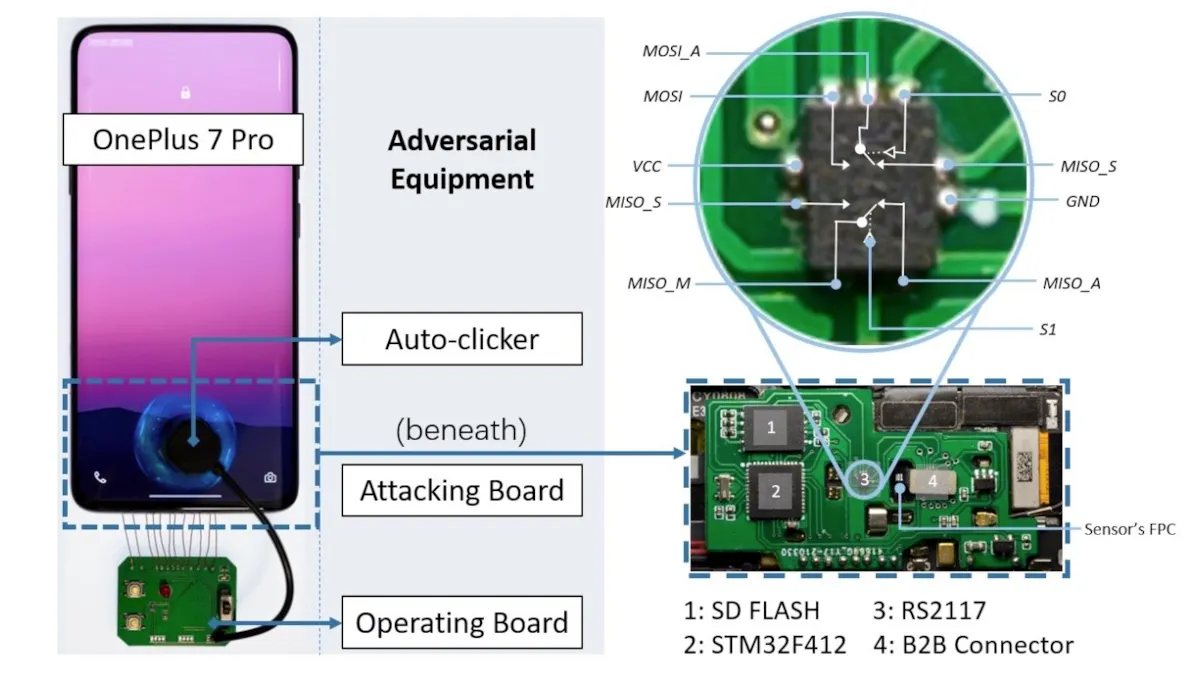
BrutePrint uses the STM32F412 microcontroller, a two-way analog switch and a dual-channel RS2117, an SD card with an 8GB capacity, and an interface for connecting the phone motherboard to the fingerprint sensor circuit. This $15 board takes advantage of vulnerabilities in Android phones to provide unlimited fingerprint guessing and will unlock the device as soon as the closest match is found in its database.
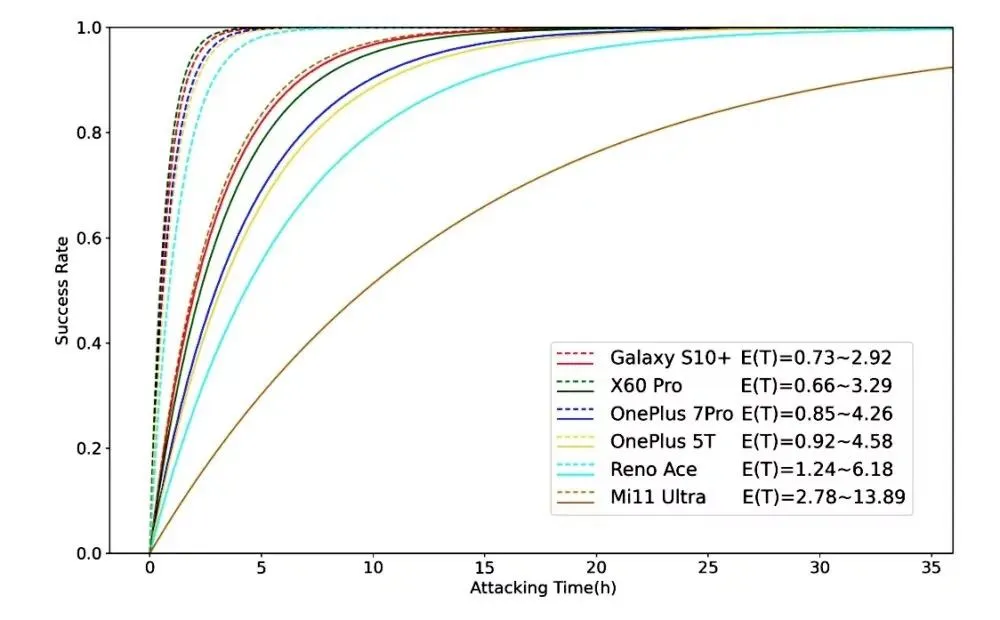
Android phones differ from one another. Researchers found that it takes between 40 minutes to 14 hours to unlock a phone. This research team tested 10 different phones, among which the Galaxy S10 Plus unlocked faster than other models (between 0.7 to 2.9 hours). The Xiaomi Mi 11 Ultra took between 2.78 to 13.89 hours to be unlocked, but researchers were unable to crack the 2nd generation fingerprint sensor of iPhone because the iOS encrypts the information available in the sensor while Android doesn’t.
Fortunately, researchers have announced that it is possible to solve the problem of bypassing fingerprint sensors on Android devices by updating the operating system. As WccfTech writes, if smartphone manufacturers and fingerprint sensors work together, they will be able to deal with such security threats. Although bypassing the fingerprint sensor on Android smartphones is very difficult under normal conditions, manufacturers of such products should take risks like BrutePrint seriously.